Configure security and access control in Application Live View
This topic tells you how to enable improved security and access control in Application Live View in Tanzu Application Platform (commonly known as TAP). Improved security and access control in Application Live View secures the REST API exposed by the Application Live View back end.
For more information about Application Live View packages, see Install Application Live View.
Security and access control overview
There is one instance of Application Live View back end installed per View profile. Multiple users access this back-end API to fetch actuator data for different applications. All the REST API calls to the back end are secured. A token must be passed to the Application Live View back end on each call to the REST API to fetch actuator data. This token is obtained from Application Live View APIServer.
The Application Live View APIServer generates a unique token upon access validation of a user to a pod. The Application Live View back end passes this token to the Application Live View connector when requesting the actuator data. The Application Live View connector verifies this token by calling the Application Live View APIServer and proxies the actuator data only if the token is valid.
The Application Live View UI plug-in part of Tanzu Developer Portal uses the preceding approach to securely query for the actuator data for a pod. It requests a token from Application Live View APIServer and passes it in the subsequent calls to the back end. This ensures that actuator data from the running application is fetched only if the user is authorized to see the live information for the pod.
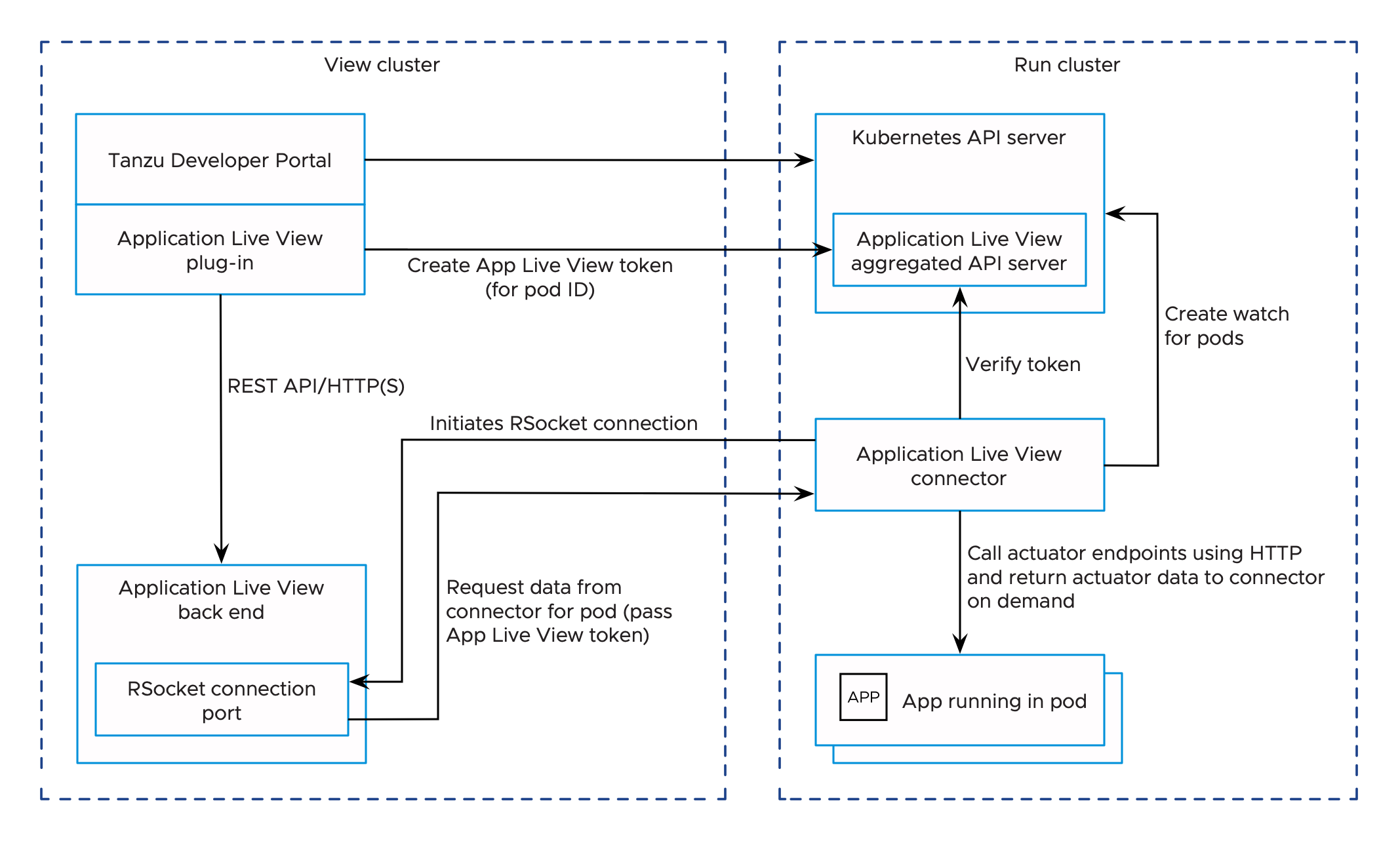
The Application Live View UI plug-in relies on Tanzu Developer Portal authentication and authorization to access the Application Live View APIServer and fetch the Application Live View tokens.
The Tanzu Developer Portal controls the access to Kubernetes resources based on user roles and permissions for each of the remote clusters. For more information, see View runtime resources on authorization-enabled clusters.
For more information about how to set up unrestricted remote cluster visibility, see Viewing resources on multiple clusters in Tanzu Developer Portal.
Prerequisites
-
You install the Application Live View APIServer package (
apiserver.appliveview.tanzu.vmware.com) in Tanzu Application Platform. For more information, see Install Application Live View APIServer. -
Assign users necessary roles and permissions for the Kubernetes clusters. For more information about managing role-based access control, see Assign roles and permissions on Kubernetes clusters
For example: If you are using Service Account to view resources on a cluster in Tanzu Developer Portal, verify that the ClusterRole has rules to access and request tokens from the Application Live View APIServer.
- apiGroups: ['appliveview.apps.tanzu.vmware.com']
resources:
- resourceinspectiongrants
verbs: ['get', 'watch', 'list', 'create']
For more information, see Set up a Service Account to view resources on a cluster.
NoteWith the Service Account approach to view resources on a cluster, every user with the Service Account Token with access to view the pods is able to see the live information in Application Live View.
Configure improved security
The improved security feature is enabled by default for Application Live View.
In a Tanzu Application Platform profile install, the Application Live View connector (connector.appliveview.tanzu.vmware.com) and the Tanzu Application Platform GUI (tap-gui.tanzu.vmware.com) are automatically configured to enable the secure communication between Application Live View components.
You can control this feature by setting the top-level key shared.activateAppLiveViewSecureAccessControl in the tap-values.yaml.
For example:
shared:
activateAppLiveViewSecureAccessControl: true
To override the security feature at the individual component level, take the following steps.
Application Live View connector
-
(Optional) Change the default installation settings for Application Live View connector by running:
tanzu package available get connector.appliveview.tanzu.vmware.com/VERSION-NUMBER --values-schema --namespace tap-installWhere
VERSION-NUMBERis the version of the package listed. For example,1.9.0.For example:
$ tanzu package available get connector.appliveview.tanzu.vmware.com/1.9.0 --values-schema --namespace tap-install KEY DEFAULT TYPE DESCRIPTION kubernetes_version string Optional: The Kubernetes Version. Valid values are '1.24.*', or ''. backend.sslDeactivated false boolean Flag for whether to disable SSL. backend.caCertData cert-in-pem-format string CA Cert Data for ingress domain. backend.host <nil> string Domain used to reach the Application Live View back end. Prepend "appliveview" subdomain to the value if you use shared ingress. For example: "example.com" becomes "appliveview.example.com". backend.ingressEnabled false boolean Flag for the connector to connect to ingress on back end. backend.port <nil> number Port to reach the Application Live View back end. connector.deployment.enabled true boolean Flag for the connector to run in deployment mode connector.deployment.replicas 1 number Number of replicas of connector pods at any given time connector.namespace_scoped.enabled false boolean Flag for the connector to run in namespace scope. connector.namespace_scoped.namespace default string Namespace to deploy connector. kubernetes_distribution string Kubernetes distribution that this package is being installed on. Accepted values: ['''',''openshift'']. activateAppLiveViewSecureAccessControl boolean Optional: Configuration required to enable Secure Access Connection between App Live View components. activateSensitiveOperations boolean Optional: Configuration to allow connector to execute sensitive operations on a running application.For more information about values schema options, see the properties listed earlier.
-
Create
app-live-view-connector-values.yamlwith the following details:To override the default security settings for connector, use the following values:
activateAppLiveViewSecureAccessControl: falseBy default, activateAppLiveViewSecureAccessControl is set to
true.The
activateSensitiveOperationskey activates/deactivates the execution of sensitive operations, such as editing environment variables, downloading heap dump data, and changing log levels for the applications in the cluster. It is set tofalseby default.To enable the sensitive operations, set
activateSensitiveOperationstotrue.activateSensitiveOperations: trueTo control permissions to execute sensitive operations at a user level, see Authorize a user to execute sensitive operations.
-
Install the Application Live View connector package by running:
tanzu package install appliveview-connector \ --package connector.appliveview.tanzu.vmware.com \ --version VERSION-NUMBER \ --namespace tap-install \ --values-file app-live-view-connector-values.yamlWhere
VERSION-NUMBERis the version of the package listed. For example,1.9.0.For example:
$ tanzu package install appliveview-connector \ --package connector.appliveview.tanzu.vmware.com \ --version 1.9.0 \ --namespace tap-install \ --values-file app-live-view-connector-values.yaml | Installing package 'connector.appliveview.tanzu.vmware.com' | Getting namespace 'tap-install' | Getting package metadata for 'connector.appliveview.tanzu.vmware.com' | Creating service account 'appliveview-connector-tap-install-sa' | Creating cluster admin role 'appliveview-connector-tap-install-cluster-role' | Creating cluster role binding 'appliveview-connector-tap-install-cluster-rolebinding' - Creating package resource / Package install status: Reconciling Added installed package 'appliveview-connector' in namespace 'tap-install' -
Verify the
Application Live View connectorpackage installation by running:tanzu package installed get appliveview-connector -n tap-installFor example:
tanzu package installed get appliveview-connector -n tap-install 5s | Retrieving installation details for appliveview-connector... NAME: appliveview-connector PACKAGE-NAME: connector.appliveview.tanzu.vmware.com PACKAGE-VERSION: 1.9.0 STATUS: Reconcile succeeded CONDITIONS: [{ReconcileSucceeded True }] USEFUL-ERROR-MESSAGE:Verify that
STATUSisReconcile succeeded.
Application Live View UI plug-in
The Application Live View UI plug-in is part of Tanzu Developer Portal. To override the default security settings for the Application Live View UI plug-in, take the following steps.
-
(Optional) Make changes to the default installation settings by running:
tanzu package available get tap-gui.tanzu.vmware.com/VERSION-NUMBER --values-schema --namespace tap-installWhere
VERSION-NUMBERis the number you discovered previously. For example,1.4.6.For more information about values schema options, see the individual product documentation.
-
Create
tap-gui-values.yamland paste in the following code:ingressEnabled: true ingressDomain: "INGRESS-DOMAIN" app_config: catalog: locations: - type: url target: https://GIT-CATALOG-URL/catalog-info.yaml appLiveView: activateAppLiveViewSecureAccessControl: falseWhere:
INGRESS-DOMAINis the subdomain for the host name that you point at thetanzu-shared-ingressservice’s External IP address.GIT-CATALOG-URLis the path to thecatalog-info.yamlcatalog definition file from either the included Blank catalog (provided as an additional download named “Blank Tanzu Developer Portal Catalog”) or a Backstage-compliant catalog that you’ve already built and posted on the Git infrastructure specified in Add Tanzu Developer Portal integrations.
-
Install the package by running:
tanzu package install tap-gui \ --package tap-gui.tanzu.vmware.com \ --version VERSION \ --namespace tap-install \ --values-file tap-gui-values.yamlWhere
VERSIONis the version that you want. For example,1.4.6.For example:
$ tanzu package install tap-gui \ --package tap-gui.tanzu.vmware.com \ --version 1.4.6 \ --namespace tap-install \ --values-file tap-gui-values.yaml - Installing package 'tap-gui.tanzu.vmware.com' | Getting package metadata for 'tap-gui.tanzu.vmware.com' | Creating service account 'tap-gui-default-sa' | Creating cluster admin role 'tap-gui-default-cluster-role' | Creating cluster role binding 'tap-gui-default-cluster-rolebinding' | Creating secret 'tap-gui-default-values' - Creating package resource - Package install status: Reconciling Added installed package 'tap-gui' in namespace 'tap-install' -
Verify that the package installed by running:
tanzu package installed get tap-gui -n tap-installFor example:
$ tanzu package installed get tap-gui -n tap-install | Retrieving installation details for cc... NAME: tap-gui PACKAGE-NAME: tap-gui.tanzu.vmware.com PACKAGE-VERSION: 1.4.6 STATUS: Reconcile succeeded CONDITIONS: [{ReconcileSucceeded True }] USEFUL-ERROR-MESSAGE:Verify that
STATUSisReconcile succeeded. -
To access Tanzu Developer Portal, use the service you exposed in the
service_typefield in the values file.
Authorize a user to execute sensitive operations
You can limit the access to execute sensitive operations to specific users. This secures operations such as editing environment variables, downloading heap dump data, and changing log levels for applications.
To authorize a user to execute these sensitive operations:
-
Create a
ClusterRolewith a rule that specifies theexecuteverb for theSensitiveOperationsAccessresource and a correspondingRoleBindingto bind it to a user:apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: alv-execute-sensitive-op-role rules: - apiGroups: ['appliveview.apps.tanzu.vmware.com'] resources: - sensitiveoperationsaccesses verbs: ['execute'] --- apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: name: alice-alv-execute-sensitive-op-role-binding namespace: dev-team-1 roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: alv-execute-sensitive-op-role subjects: - kind: User name: "alice@example.com" apiGroup: rbac.authorization.k8s.io -
If you are using service account to view resources on a cluster in Tanzu Developer Portal, create a
ClusterRolewith a rule that specifies theexecuteverb for theSensitiveOperationsAccessresource and a correspondingRoleBindingto bind it to thetap-guiservice account:apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: alv-execute-sensitive-op-role rules: - apiGroups: ['appliveview.apps.tanzu.vmware.com'] resources: - sensitiveoperationsaccesses verbs: ['execute'] --- apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: name: alv-execute-sensitive-op-role-binding namespace: dev-team-1 subjects: - kind: ServiceAccount namespace: tap-gui name: tap-gui-viewer roleRef: kind: ClusterRole name: alv-execute-sensitive-op-role apiGroup: rbac.authorization.k8s.io -
(Optional) Edit the tap-gui cluster role
k8s-readerto add a rule that specifies theexecuteverb for theSensitiveOperationsAccessresource in a single cluster setup:kubectl edit clusterrole k8s-reader -n tap-gui -
Add the following rule to the cluster role:
- apiGroups: ['appliveview.apps.tanzu.vmware.com'] resources: - sensitiveoperationsaccesses verbs: ['execute']Note
Executing sensitive operations is deactivated by default. You can enable it at the cluster level by setting the
activateSensitiveOperations: truekey in the appliveview_connector config or at the individual user level by assigning the roles and permissions mentioned earlier.