Create suppression policies for security posture findings in VMware Tanzu Platform hub
As an administrator or application owner, you must ensure the most critical findings are resolved quickly while managing signal noise from findings that are high in volume and have a low priority or blocked resolution. You can use suppression policies to hide findings across multiple accounts in a single action, or to stop tracking findings completely for policies that don’t fit your organization.
Before you begin
Verify user roles and permissions:
- Administrator permissions are required to control policies and approve or deny suppressions.
- Analyst permissions are required to submit a suppression request.
How to suppress findings from a suppression policy
You can create a suppression policy that uses criteria like accounts, policies, environments, and so on to suppress the findings from one or more policies across a project or organization. For example, to suppress all findings for an open alternative HTTP port on an AWS EC2 security group in a development environment, follow these steps.
NoteSuppression policies are only available for findings of violation or threat type associated with a posture policy. For drift findings associated with policy templates, suppress them individually in Tanzu Platform hub by clicking Security Posture > Findings .
- In Tanzu Platform hub, click Security Posture > Suppressions.
- Click New Suppression.
- For Context, select organization if available, or select a specific project.
- For Duration, select the length of time that the suppression must remain in effect.
- Click Next.
-
To determine how your suppression policy must apply, add criteria.
For example, the following selections suppress all findings for the selected policy on every cloud account added to the
devenvironment, with regard to the context you selected in the previous step.Sample criteria for suppression policy
Criteria Value Cloud Account All current cloud accounts Policy EC2 security group should restrict public access over IPv4 to alternative HTTP port (8888) Environment Dev -
Click Next.
- Review your selections, then provide a business justification for the request in the Reason area.
- Click Submit.
How to approve, deny, update, or resubmit a suppression request
Depending on your permissions, to manage suppression requests, you can take several actions in Security Posture > Suppressions.
- If you’re a Tanzu Platform hub administrator, you can review suppression requests under the Open tab, and approve or deny them.
- If you submitted a suppression request and received an approval, you can find it under the Active tab and make updates, such as requesting an extended duration, or remove it if the suppression is no longer needed.
- If you submitted a suppression request and received a denial, you can find it under the Denied tab, and resubmit it with additional details.
How to create a business justification template for suppression requests
Before users can submit suppression requests, they must provide a business justification. Tanzu Platform hub administrators can create a template that helps users understand any specific information they must include with their requests.
- In Tanzu Platform hub, click Security Posture > Suppressions.
-
Click the cog icon.
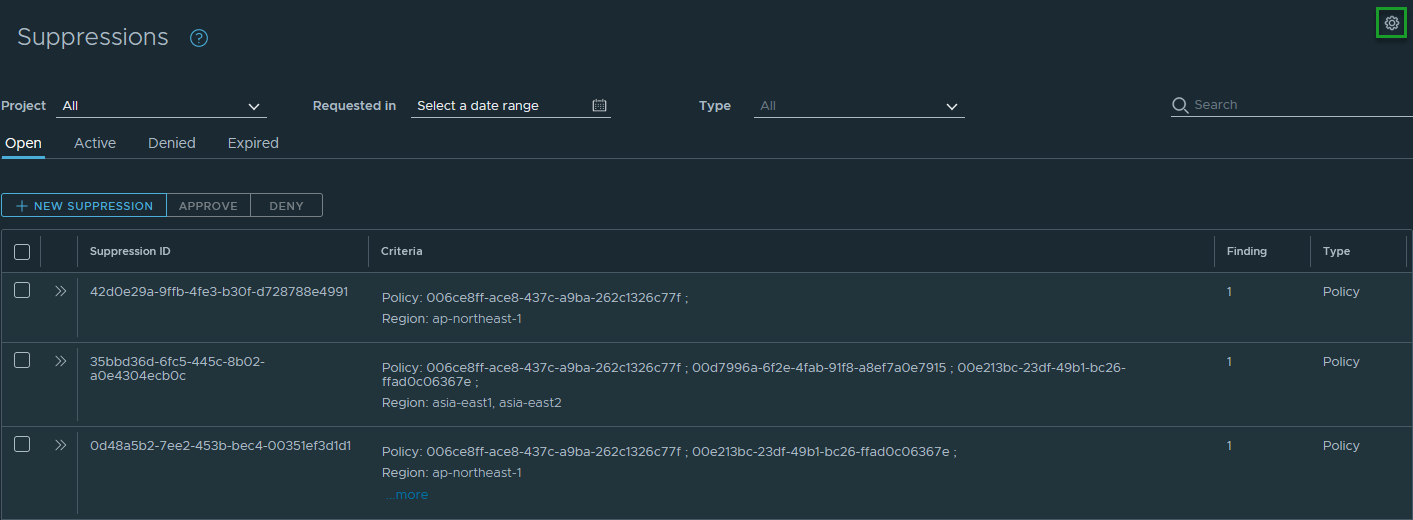
-
Type or paste your template in the entry area. Refer to this example:
What is the business justification? Does this resource contain production data? (Yes/No) What measures are in place to mitigate the security risk? What level of effort is required to remediate the violation? (Low/Medium/High) -
Click Submit.
Your template now appears in the Reason area whenever a user creates a suppression request.
How to stop receiving findings for non-relevant posture policies
If you determine the findings from a posture policy are not relevant to your security goals, or that they are contrary to business requirements, you can deactivate the policy to stop receiving those findings. Using the previous example for a suppression policy, let’s say your company requires the alternative HTTP port to be open. In that case, you don’t ever want to receive findings from this policy on any accounts that you monitor, so you can deactivate the policy.
Note: Posture policies are controlled at the level of your Tanzu Platform cloud services organization, so it’s not possible to deactivate a policy at the project context. If you’re getting too many unnecessary findings for accounts in a project and you can’t deactivate the security policy because it’s required by another project, use a suppression policy instead.
- In Tanzu Platform hub, select Security Posture > Policies > View (Posture policy).
- Locate the policy named
EC2 security group should restrict public access over IPv4 to alternative HTTP port (8888)with filters and search terms. -
Select the check box next to the policy, then click Deactivate.
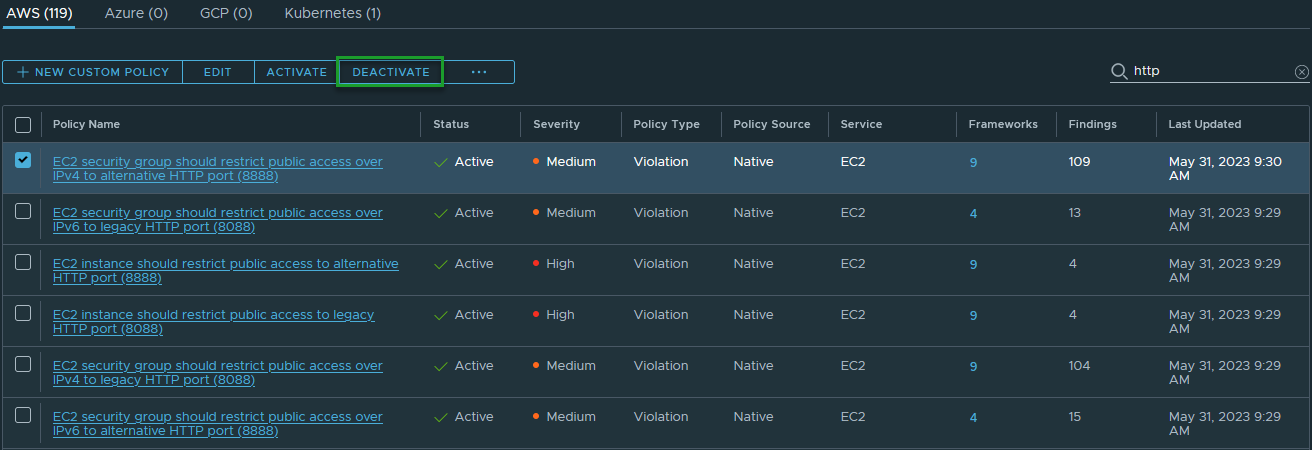
-
Enter a reason why the policy must be deactivated, then click Disable.
Tanzu Platform hub resolves any open findings for a deactivated policy and stops reporting additional findings going forward. To start receiving findings again, you can activate the policy at any time.
Parent topic:Investigate VMware Tanzu Platform hub Security Posture findings